Eric Pudalov
Writer, Editor, Privacy & Security Advocate
Eric Pudalov

My name’s Eric. Admin by day. Security and privacy advocate by night.
Security, privacy software, and online anonymity are my favorite topics to write about. However, my foray into freelance writing began with the now-defunct Yahoo! Contributor Network, where I wrote quite a few music and technology reviews, as well as interviews with musicians, and other entertainers. You may have also seen some of my writing on Examiner.com as well as Tools4Hackers.com. I currently am a contributing security and privacy writer at Darkrebel.net and occasionally I spin up marketing content for websites as needed.
Looking for a writer with amazing copy-editing skills who also knows their way around code? I’m currently looking for freelance, part-time, or full-time gigs. You will appreciate working with “the human spellchecker.”
Eric Pudalov
Battle of the Secure Smartphones
While no internet-connected device is 100% secure, some definitely are more armored than others. In the smartphone arena, several phones consistently rank among the best.
To which ones might I be referring? The Kali Linux NetHunter 3.0, Copperhead OS, and Blackphone 2 are a few favorites. Obviously these devices can be used by more than just those who explore the dark web, but if you’re someone who does, a little protection can’t hurt, right?
Those of you in the pen testing field already know the Kali Linux name. Given that it’s almost synonymous with security, I expected nothing less of the latest NetHunter distro.
NNetHunter 3.0 supports the following attacks (and tools):
- Wireless 802.11 frame injection and AP mode support
- USB HID Keyboard Attacks
- BadUSB MITM Attacks
- Full Kali Linux toolset
- USB Y-cable support in the Nethunter kernel
- Software-defined radio support
In addition, the NetHunter features many of the pentesting weapons that its desktop counterpart has in its arsenal, such as Aircrack-ng (a suite of tools to assess Wi-Fi network security); BBQSQL, which simplifies blind SQL injection tests; and Ghost Phisher, a wireless and Ethernet security auditing and attack software program. So, great, I have an armory of “attack” tools, but can the NetHunter defend itself? Of course!
While it includes a number of tools for defensive purposes as well, one of its more impressive features is the ability to cause the Linux Unified Key Setup (LUKS) to self-destruct, a.k.a. a “nuke option.” (This feature is available on its other platforms as well).
The self-destruct process hasn’t officially been implemented yet, but if you’re already a Kali user and would like to try it out, there are more detailed instructions here:
Testing the LUKS Nuke Patch
Beyond this, the same tools that can be used to simulate attacks against other systems could be used to find vulnerabilities on yours. As with the versions of Kali on other platforms, however, I wouldn’t recommend them to a beginner with Linux distros. It’s possible that it could either prove frustrating, or you might do something with it that you don’t intend. Its tools have a specific user base in mind.
One possible security issue to note: if you’re using an older device (such as the Nexus 7) with Nethunter 3.0, it may have trouble encrypting the device. A collaborator named jmingov on Github suggested the following fix for this problem:
“Atm, the easiest way is to remove the chroot from Nethunter app, encrypt the device, and then reinstall the chroot.” (For the full conversation, see GitHub: Kali NetHunter issues.) Overall, however, it seems to be well protected."
Ricochet Messenger Review
Ricochet is an anonymous messaging app that uses the Tor network. They describe themselves as “…a different approach to instant messaging that doesn’t trust anyone.” For those who already use Tor for privacy or are interested in encrypted messaging, this can be a useful alternative to other messengers like Signal.
Ricochet URL
Ricochet GitHub URL
How Ricochet Works
Ricochet uses the Tor network to speak with your contacts, as opposed to a central messaging server. When starting a conversation with someone, the app creates a hidden service, through which you can reach your contacts without revealing your location or identity. It’s not unlike the purpose of browsing the web through Tor itself.
Rather than a username, Ricochet gives you a unique identifier, such as “ricochet:rs7ce36jsj24ogfw,” through which other users can contact you. When another user wants to send you a “contact request” (i.e. ask to be added to your contact list), this is the address they’ll use. Thus, when you communicate with someone through Ricochet, their identity consists of cryptographic hashes, much like the characters in Tor URLs (e.g. “xtmyl24o3cc7oc22.onion”).
One advantage that Ricochet has, in this sense, is that your contact list is only known to your machine, and not outside servers or network traffic surveillance.
Ricochet Pricing
 In this instance, pricing is irrelevant, because Ricochet is free and open source software. Its funding comes from donations and sponsors, such as Blueprint for Free Speech, a nonprofit organization, and the invisible.im project, both of whom support freedom of expression in the IT industry. Because it is open source, they are looking for people to contribute to its code and make improvements, so feel free to help out if this is your area of expertise.
In this instance, pricing is irrelevant, because Ricochet is free and open source software. Its funding comes from donations and sponsors, such as Blueprint for Free Speech, a nonprofit organization, and the invisible.im project, both of whom support freedom of expression in the IT industry. Because it is open source, they are looking for people to contribute to its code and make improvements, so feel free to help out if this is your area of expertise.
Ricochet Platforms
 Ricochet is available for Windows, Mac, and Linux OS’s. On their homepage, there are links to download versions for each of these operating systems. Alternately, you can build it from source, if you’re the coder type and want to customize it. In that case, visit its GitHub repository, linked to above.
Ricochet is available for Windows, Mac, and Linux OS’s. On their homepage, there are links to download versions for each of these operating systems. Alternately, you can build it from source, if you’re the coder type and want to customize it. In that case, visit its GitHub repository, linked to above.
Ricochet Features
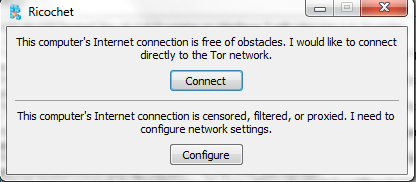 As explained above, Ricochet keeps your messaging anonymous by using the Tor network. Each of your contacts is identified via a Tor hidden service. Just to clarify, you don’t need to run the Tor Browser in order to use Ricochet; it will connect to the Tor network by itself.
Just as when you use the Tor Browser, Ricochet has different options for connecting to the network. Under its Preferences link (which is a little gear icon), you can configure how Ricochet connects to Tor:
As explained above, Ricochet keeps your messaging anonymous by using the Tor network. Each of your contacts is identified via a Tor hidden service. Just to clarify, you don’t need to run the Tor Browser in order to use Ricochet; it will connect to the Tor network by itself.
Just as when you use the Tor Browser, Ricochet has different options for connecting to the network. Under its Preferences link (which is a little gear icon), you can configure how Ricochet connects to Tor:
If you live in an area where Tor is unrestricted, simply click the “Connect” button, and you should be able to connect to the Tor network without problems. On the other hand, if you live in an area where Tor (or the internet in general) is restricted, click the “Configure” button.
From there, you can configure how you connect to Tor:
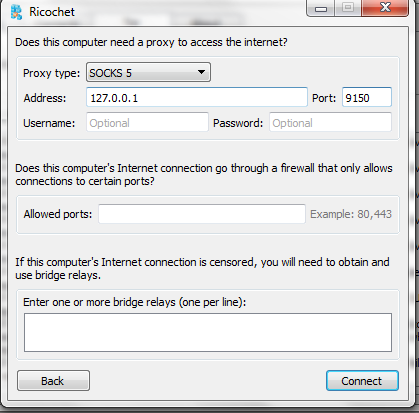 Choose a proxy type (e.g. SOCKS5), an IP address (e.g. 127.0.0.1), and a port (e.g. 9150). Then, under the section that reads “Does this computer’s Internet connection go through a firewall that only allows connections to certain ports?,” you can list specific ports if that applies to the situation. Please note that this is not necessary unless the firewall is restricting your connection.
Choose a proxy type (e.g. SOCKS5), an IP address (e.g. 127.0.0.1), and a port (e.g. 9150). Then, under the section that reads “Does this computer’s Internet connection go through a firewall that only allows connections to certain ports?,” you can list specific ports if that applies to the situation. Please note that this is not necessary unless the firewall is restricting your connection.
Below this, it reads "If this computer’s Internet connection is censored, you will need to obtain and use bridge relays." Bridge relays are Tor relays that aren’t listed in the main Tor directory. If you live in a country with strict internet filtering, you can use these bridge relays to connect to the Tor network. In the box underneath the aforementioned message, enter the IP addresses of the bridge relays you wish to use, one per line, and then< click “Connect.” You should now be able to get Ricochet to connect to Tor (in theory). Of course, if you’re fortunate enough not to have to use bridges or pluggable transports, then you can skip all this information.
Ricochet User Interface
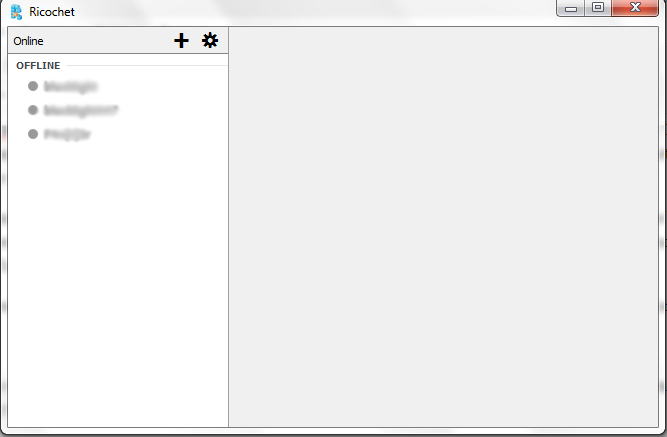 As you can see, Ricochet has a very simple, basic interface, which to some may be a disadvantage. Compared to other messengers, it doesn’t have much “flare,” but that isn’t really its purpose.
As you can see, Ricochet has a very simple, basic interface, which to some may be a disadvantage. Compared to other messengers, it doesn’t have much “flare,” but that isn’t really its purpose.
In other words, you can’t use things like emojis or different fonts, nor does it have the ability to upload profile pictures or things like that. At the very least, you can enable audio notifications so that you’re aware when you receive a new message. To sum up, its visual aspects aren’t its strong suit, but in terms of encryption and privacy, it works quite well.
Comparison with Other Messengers
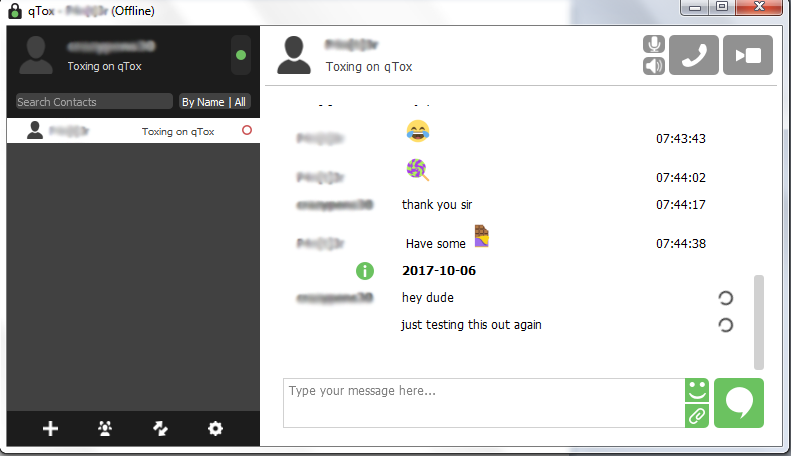 There are several other messengers available that use various forms of encryption, but each works a bit differently, and not all are decentralized. One that is somewhat similar is Tox, which, like Ricochet, is decentralized and also conceals your identity from all except friends.
There are several other messengers available that use various forms of encryption, but each works a bit differently, and not all are decentralized. One that is somewhat similar is Tox, which, like Ricochet, is decentralized and also conceals your identity from all except friends.
As on Ricochet, when you add a friend on Tox, their ID consists of cryptographic hashes, like this: 56A1ADE4B65B86BCD51CC73E2CD4E542179F47959FE3E0E21B4B0ACDADE51855D34D34D37CB5. You can then customize the name as you wish. The same is true of Ricochet; once you add a friend by their crypto-identifier, you can rename them so they’re easier to recognize.
One difference with Tox, however, is that it requires the use of bootstrap nodes in order for each client to recover a list of other clients who are currently connected to the pool. With Ricochet, you only need your contacts ID.
Although some might compare Ricochet to messengers like Signal, Signal is a bit different, in that it is produced by Open Whisper Systems (and therefore relies on a central authority). Given that some companies have been forced to release customer data to law enforcement, or have been hacked and lost private information, a messenger like Ricochet seems ideal.
Plus, most mainstream messengers (including Signal) require a centralized server. In the case of Ricochet, you are both the server and the client at the same time, as counterintuitive as that might seem (i.e. every user is a server). Furthermore, messengers that rely on a central server can collect metadata about their users, meaning that if they were forced to hand over information about them, it would be easy to do so.
On the other hand, in the case of Ricochet, because all of its traffic goes through the Tor network, it would be extremely difficult to collect any such metadata. To sum up, in terms of anonymity, Ricochet outperforms its competitors in several aspects, even if it doesn’t look as appealing.
Support
 If you need support with Ricochet, you must contact its developers via the issue tracker on GitHub. While this may seem unconventional to some, it actually is quite helpful, as it is an ongoing project, and the developers have an interest in solving any issues that may come up. It’s also a good place to suggest new features or other ideas that you may have.
If you need support with Ricochet, you must contact its developers via the issue tracker on GitHub. While this may seem unconventional to some, it actually is quite helpful, as it is an ongoing project, and the developers have an interest in solving any issues that may come up. It’s also a good place to suggest new features or other ideas that you may have.
Pros and Cons
Pros
- Better privacy and anonymity than most messaging apps
- Uses the Tor network
- Can be used in countries with strict internet censorship
- Relies only on a P2P connection
Cons
- Very basic user interface, without much personalization
- Lacks a variety of features
- Still in alpha stage and may have bugs
Puerto Vallarta: Discover Your Mexican Paradise
I once spent New Year’s Eve in Puerto Vallarta, Mexico, and I don’t think I’ll have another quite like it. We were within a few steps of an extraordinary beach, which melded with the crystal blue ocean waves.
Far from mere sunrises, the ones we saw were breathtaking bursts of flame, peeking out over the horizon, encapsulating that brief moment in paradise. Of course, this was not merely a visual experience; it had its fair share of action.
My family and I, one morning, took the opportunity to go ocean kayaking. It was my first time attempting this feat, so I was unsure of what to expect! Our teacher had a “hit the ground running” approach to his lessons.
We pushed ourselves out into the massive waves that were characteristic of this particular beach, and the teacher kept saying, “Keep the boat straight! Keep the boat straight!” As much as I attempted to follow his instructions, my kayak flipped over and crashed upon my head - very painfully, I might add. The teacher helpfully said, “I thought I told you to keep it straight!”
After four attempts, I finally managed to stay afloat, and paddled myself across to the smaller island which was our destination. Being that the initial launch was so difficult, reaching the end was a true victory! In spite of that slight challenge, I have to credit this vacation, as it instilled in me a love of kayaking which I still treasure to this day.
A second adventure saw us galloping on small horses through a dense jungle, giving us a small taste of what Indiana Jones might have felt like. This, too, was initially challenging, as my horse riding experience was minimal. At one point, my horse took off striding down the path, and our guide had to intervene. Of course, experiences like this were what made the trip memorable.
Finally, when it came to New Year’s Eve itself, we basked in the violet Puerto Vallarta evening, indulging a tequila or two - or was it three? Regardless, it was one of those moments where time seemed to slow to a crawl, allowing me to forget my college cares at the time.
And let’s not forget - these folks know how to party! Rhythmic dancing, fiery trumpets, and clashes of exotic percussion ignited our inner vitality as we counted down...4...3...2...1…”Feliz año nuevo!” For all its moments, delectable and dizzying, Puerto Vallarta has truly taken up residence in my memory.
More Ways to Earn Bitcoin in 2019
As with “normal” money, there’s no simple way that works 100% of the time, but there are several methods; some take much longer than others and don’t necessarily deliver on their promises.
As Bitcoin Chaser mentions on The Best Bitcoin Apps of 2019, there are several mobile apps that help you earn bitcoin, although it probably takes a lot of time to earn a significant amount.
The first app they mention, Bitcoin Billionaire, is just a game that plays with the idea of bitcoin, but doesn’t actually pay anything. The second one, Free Bitcoin, does, although as you might expect, this doesn’t happen overnight.
The way this app works is that you watch ads which, in turn, pay you satoshi (and eventually BTC). Be that as it may, if you go by the reviews on the Play Store, you can only earn up to a certain amount before the app says that your account is “locked” and it cannot deposit the coins. In all honesty, the whole thing sounds like a scam, but what did you expect?
There was an app called BitMaker, through which I earned my first fraction of a bitcoin. The app in question is now called Storm Play, but the concept is more or less the same: try out new games and products or complete tasks and earn bitcoin in the process. As with any other apps of this type, it can take quite some time to earn a significant amount, but at the very least, I can say that this app did pay eventually.
For instance, one of the tasks you can do, sponsored by Groupon, is this: Make a purchase on Groupon.com. Purchase value must exceed $10. Groupon Bucks may not be used. Only the first purchase per click will be considered.
Another involves the game Vikings: War of Clans (the RPG, that is), which you may recognize from some YouTube ads if you haven’t played it already. It’s fun and all, but what’s the catch? You have to install a separate app, play the game, and reach level 12. Upon doing so, you’re rewarded with 570,000 “Bolts” (a cryptocurrency that’s the smaller unit of Storm Tokens). Think of it this way: Bolts are to satoshis as Storm Tokens are to bitcoins.
One other downside to this app, unfortunately, is that it consumes a lot of battery power (which is probably the case with any bitcoin mining/earning app). If that isn’t a problem for you, then try this one out.
A third app of this type is called Alien Run (another game), and like the previous ones, you earn bitcoin by playing the game and watching in-game ads (which is where the payout comes from). Like the other apps mentioned here, it takes quite a bit of playing to actually earn much, and it’s questionable as to whether the time and effort is worth it.